Mitm It Certificate

This brittle model allows to set up lawful or unlawful man in the middle attacks.
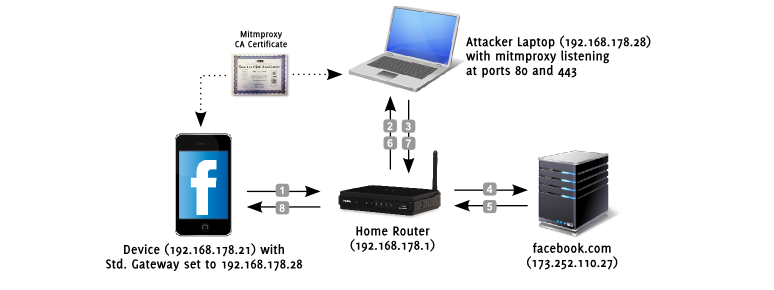
Mitm it certificate. Mitmproxy then uses the provided certificate for interception of the specified domain instead of generating a certificate signed by its own ca. The certificate file is expected to be in the pem format. Only the best comes from mi t m manufacturing a wide range of industrial cleaning equipment pressure washers pressure washing equipment pressure washer parts water treatment systems and more. The web page that will open offers mitmproxy certificate to be installed.
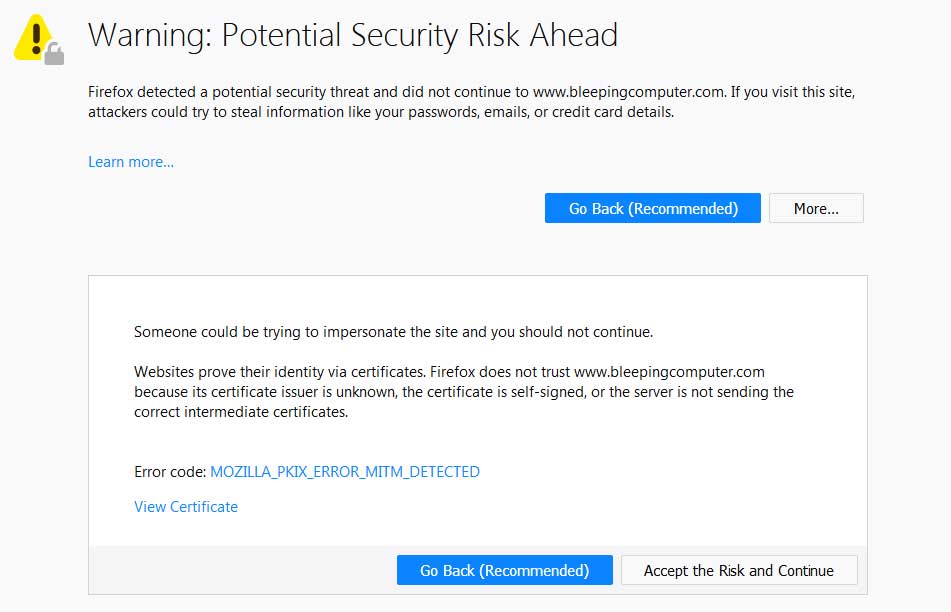
To answer https while offline for caching purposes consider to use ganskeflittleproxy parentsee aldo cortesi for a detailed description of proxy interception processes. The current model of trust of internet employs hundreds of cas. Each time you want to check whether there is mitm visit this website and check whether it presents an ev ssl certificate. Mitmproxy includes a full ca implementation that generates interception certificates on the fly.
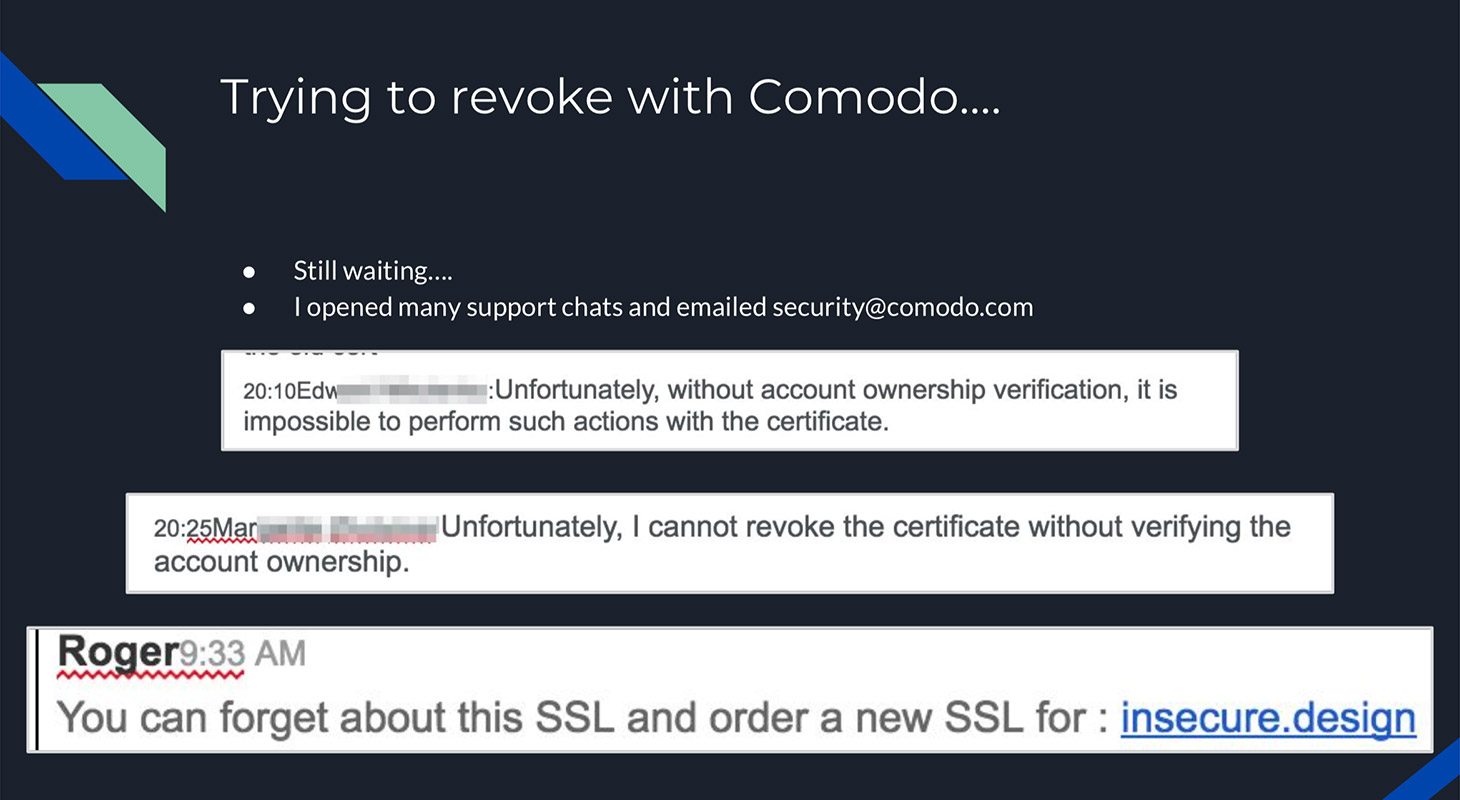
Our answer to this conundrum is to become a trusted certificate authority ourselves. You can include intermediary certificates right below your leaf certificate so that your pem file roughly looks like this. The simplest way to register mitmproxy certificate on a device is to visit mitmit url after connecting the device through mitmproxy. Tuesday march 14th 2017.
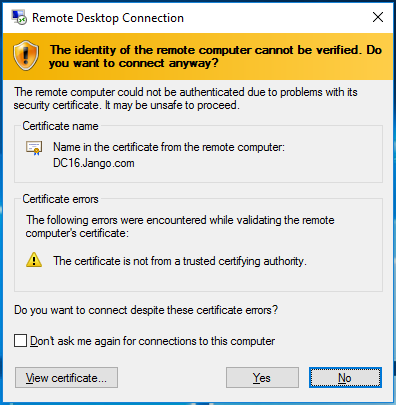
Now you are ready to intercept http and https communication. How ssl certificates protect you from man in the middle attacks. Littleproxy mitm is an extension for littleproxy which provides all the filter capabilities of littleproxy with https sites too. In cryptography and computer security a man in the middle attack mitm is an attack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each otherone example of a mitm attack is active eavesdropping in which the attacker makes independent connections with the victims and relays messages between.
Despite the many shortcomings of the ca system as it exists today this is usually fatal to attempts to mitm a tls connection for analysis. It aims to support every java platform including android. But it is more likely that mitm is possible if self signed certificates are used because the clients dealing with self signed certificates often deal with these in the wrong way. Using self signed certificates does not mean mitm is possible and using a certificate issued by a public ca does not mean mitm is impossible.