Nist Continuous Monitoring Plan Template

Templates nist publications learning.
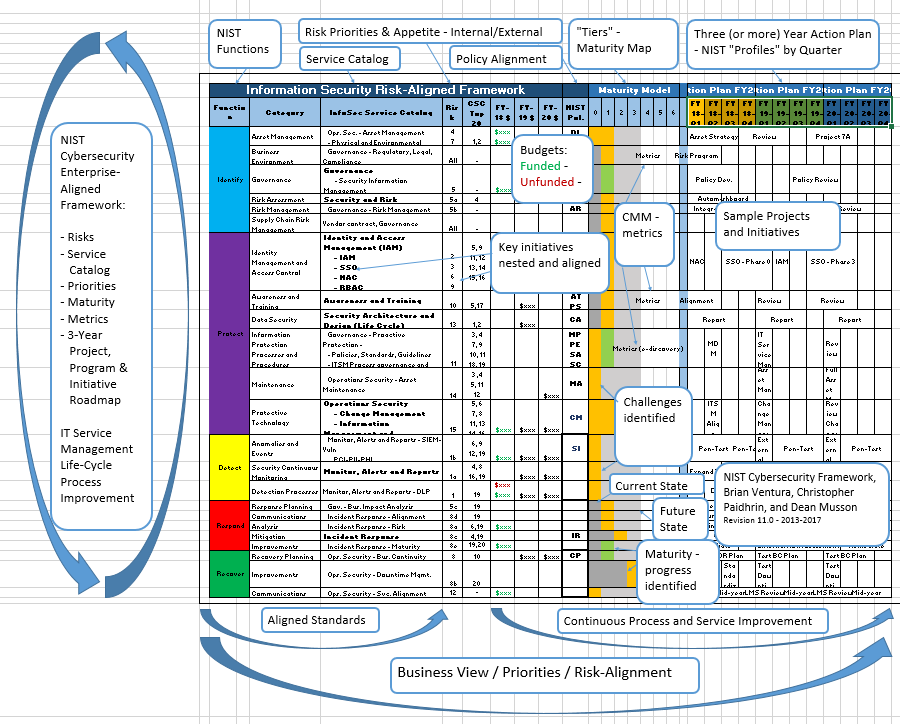
Nist continuous monitoring plan template. The templates and checklists are the various forms needed to create an rmf package and artifacts that support the completion of the emass registration. The rmf when used in conjunction with the three tiered enterprise risk management approach described in nist sp 800 39 tier 1 governance level tier 2 missionbusiness process level and tier 3 information system level and the broad based continuous monitoring guidance in nist sp 800 137 provides a comprehensive process for developing. 3551 et seq public law pl 113 283. Nist is responsible for developing information security standards and guidelines including minimum.
Can make the process of continuous monitoring more cost effective consistent and efficient. Define a continuous monitoring strategy based on risk tolerance that maintains clear visibility into assets and awareness of vulnerabilities and utilizes up to date threat information. Fedramp is following the nist guidance and this document describes how fedramp intends to implement it. Noaa continuous monitoring guidance for annual security control assessments v4 february 2012 60 policy as required by doc itspp section 447 the nesdis specific continuous monitoring process and procedures shall align with the doc and noaa prescribed practices for implementing an effective continuous monitoring planning process.
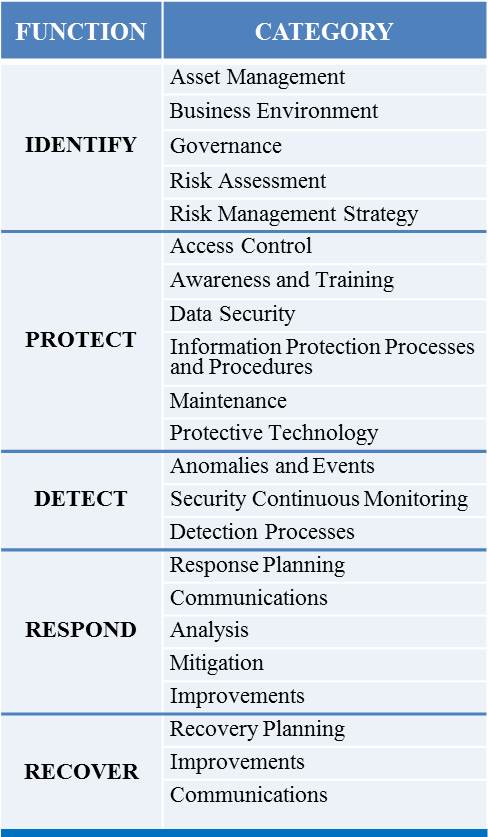
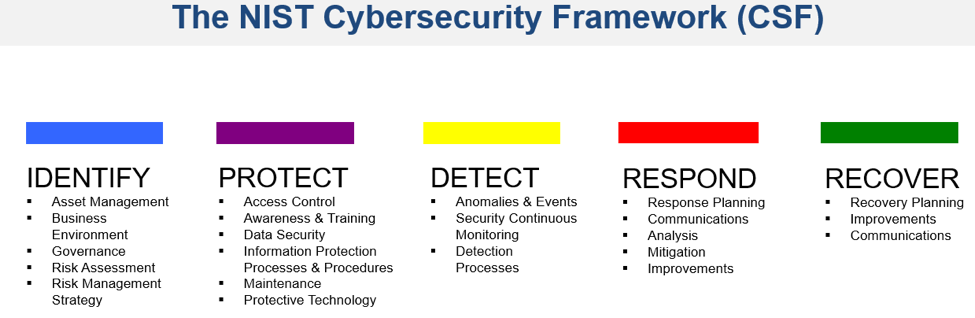
Provides a structured framework for aggregating system vulnerabilities and deficiencies through security assessment and continuous monitoring efforts. Many of the technical security controls defined in nist special publicationsp 80053 recommended secu rity controls for federal information systems and organizations as amended are good candidates for monitoring using automated tools and techniques. This publication has been developed by nist to further its statutory responsibilities under the federal information security modernization act of 2014 44 usc. As defined by nist the process for continuous monitoring includes the following initiatives.
This form provides the jab reviewers and pmo with an executive summary of the monthly continuous monitoring submission from a csp. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitorin information security continuous monitoring iscm for federal information systems and organizations nist. This template is intended to be used as a tracking tool for risk mitigation in accordance with csp priorities.